7-Zip is a free open source DMG extractor software for Windows. It is a popular file. If you decrypt a file using this option, only the file will be decrypted. If you decrypt a folder using this option, the folder, subfolders and files will be decrypted. Right click or press and hold on a folder you want to decrypt, and click/tap on Properties. After the encryption it will rename the files as a HTML file, with inside the original encrypted file. If you try to open any of these encrypted files, you will be redirect to the malcious web page, which is currently at xblblock.com, that will display the same screen of the “Decrypt Protect MBL Advisory” and will try to persuade you to pay the ransom in the form of a MoneyPak voucher. Cracking encrypted disk image, AKA DMG is feasible, but, and there are many buts, is extremely, extremely time consuming. If you do not remember at all the password, or if you attempt to crack in 'blind mode', you will probably need to teach your kids how to do it: By the time you'll have a fighting chance, you'll be long dead.
- Decrypt Dmg File Without Key Free
- Decrypt Dmg File Without Key Download
- Decrypt Dmg File Without Key Code
Let's cut to the chase right now:
Cracking encrypted disk image, AKA DMG is feasible, but, and there are many buts, is extremely, extremely time consuming.
If you do not remember at all the password, or if you attempt to crack in 'blind mode', you will probably need to teach your kids how to do it: By the time you'll have a fighting chance, you'll be long dead.
Step 1: Write down everything you can remember about the forgotten password, i.e what you could have used, and what you are sure not to have used, i.e. never used a space or a '@' sign.
Step 1a: If you remember enough of your password, or if you are just missing trailing numbers i.e Mypassword???? >> MyPassword1234 and do not remember if it's 1234 or 4321, or 9999, Just use CrowbarDMG and a Wordlist.
For good Wordlists, go here!
If you need to create a specific wordlist (because you remember what you may have used and, most importantly, what you may have not used, go here and look for Wordlists On Demand)
Warning!: CrowbarDMG is slow!
CrowbarDMG is basically a GUI for the hdiutil command
ETA for trying 9999 passwords: About 3 hrs
99,999 passwords: About 30 hrs
999,999 passwords: About 300 hrs Or 12 days ....
Step 2: Do you know how to compile and use John The Ripper? I mean 'use it! including editing Rules, etc?
--> No? Proceed here. Read carefully. Pause. Repeat.
--> Yes! Ok, Sure?
1) Download JTR, version Bleeding Jumbo by Magnum
As of Aug 2013, it's here otherwise here
2) Compile. Don't forget to edit the Makefile and John.conf. Check for CUDA and OMP/MPI RUN. Creating a new Charset? that could be wise...
3) Run dmg2John.py to extract the hash
python [path to file ]dmg2john.py [path to file] myfile.dmg > dmg.txt
4) Edit/Create your rules as needed
5) ./ John etc (Run Baby, run ....)
6) There is always Hashcat (Win/Lin)
7) Because most you have seen, in movies, Hackers cracking an AES within minutes, you'll try without thinking too much about it.
It's going to leave you with a lot of time to read ....
Enjoy ...
8) Without going into too much details, the use of GPU assisted is highly recommended. If you have one of those ones, you'll most likely increase your speed by a factor of 1000, sometimes 10,000 times faster.
☞ Password Cracking AES-256 DMGs and Epic Self-Pwnage
(The Keyword here is: 25 GPU)
☞ 'If you have thought about a new cracking method, It's probably already in JtR'
(Matt Weir) (Quoted liberally)
☞ 'I don't care if the NSA teams up with the KGB, a full random 15Ch long AES is practically unbreakable in a lifetime.
(Matt Weir, Quoted Very Liberally, From circa 2009)
EPAG: Empirical Poke-Around Graph
Markov Probabilities

Category: «Cryptography», «Elcomsoft News», «General», «Security»
In the world of Windows dominance, Apple’s Mac OS X enjoys a healthy market share of 9.5% among desktop operating systems. The adoption of Apple’s desktop OS (macOS seems to be the new name) is steadily growing. This is why we are targeting Mac OS with our tools.
This time, let’s talk about Mac OS X user account passwords. Not only will a user password allow accessing their Mac, but it will also allow decrypting FileVault 2 volumes that are otherwise securely encrypted with virtually unbreakable XTS-AES.
Attacking FileVault 2
FileVault 2 is Apple’s take on whole-disk encryption. Protecting the entire startup partition, FileVault 2 volumes can be unlocked with either of the following:
- 256-bit XTS-AES key
- Recovery Key
- User password from any account with “unlock” privileges
There is also an additional unlock method available called Institutional Recovery Key. These recovery keys are created when system administrators enable FileVault 2 encryption with FileVaultMaster.keychain. This method requires additional steps to activate, and is typically used in organizations with centralized keychain management.
256-bit XTS-AES Key
Location: RAM (only while the encrypted volume is mounted)
The 256-bit XTS-AES key is the actual encryption key that is used by the system to encrypt and decrypt data. This is a binary key. Once the FileVault 2 volume is unlocked, the XTS-AES key is stored in the computer’s RAM.
In order to recover these keys, one would need to dump the content of the computer’s RAM into a file. Note that it is no longer possible to run a FireWire attack on locked or sleeping Macs due to Mac OS X security restrictions, so the RAM capturing tool must be executed on a running computer with FileVault 2 container unlocked and a user logged in.
Recovery Key
Location: printed notes, Apple cloud
Extraction: search, cloud acquisition (coming to Elcomsoft Phone Breaker 6.0), request from Apple
Similar to BitLocker, FileVault 2 employs Recovery Keys to enable users unlock their encrypted volumes if the disk is moved to a different device or if no user account with ‘unlock’ privileges is present in the system. Once FileVault 2 is enabled, the system creates and displays a recovery key. According to http://eprint.iacr.org/2012/374.pdf, the recovery key contains 120 bits (we didn’t check) that are encoded with all letters and numbers 1 through 9, and formatted to look like this:
Decrypt Dmg File Without Key Free
XDFG-EE8G-KF89-S0FS-9F7Y-XFH8
The user has an option to store the key with Apple. If the user agrees, the recovery key gets stored in the iCloud account associated with the user’s Apple ID (which is required to use the service).

While brute-forcing a 120-bit key seems easier than attempting to brute-force a 256-bit key, the security of a 120-bit key is still enough to make the attack unfeasible. This key is only useful if you can obtain it by searching the premises, downloading from the user’s iCloud account or requesting from Apple (if you have a warrant).
Extracting FileVault 2 Keys from iCloud
It is possible to extract a backup FileVault 2 key from the user’s iCloud account. The backup key can be extracted, processed and converted into a binary 256-bit XTS-AES key that can be used to decrypt the volume.
We are currently finalizing development of a tool for extracting and using FileVault 2 recovery keys to mount FileVault 2 volumes. In order to extract the key, you’ll be able to use Elcomsoft Phone Breaker 6.0 (scheduled for release next month). Once the tool is released, you’ll need to do perform the following steps:
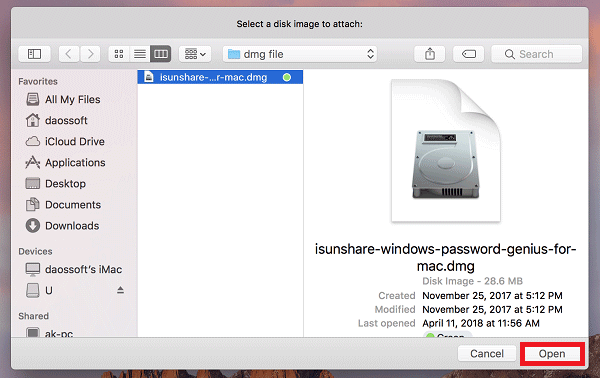
- Launch Elcomsoft Phone Breaker and choose iCloud. Select “Decrypt FileVault image”.
- Specify path to the forensic image of the encrypted volume. Elcomsoft Phone Breaker accepts raw disk images (.dd), EnCase image files (.e01), and Apple Disk Images (.dmg).
- In a case the image contains several encrypted partitions, choose the one which you would like to mount (you may see more than one FileVault 2 volumes if several OS X installations are present).
- Elcomsoft Phone Breaker displays Apple ID that has the Recovery Key stored in its iCloud account.
- Provide authentication credentials (Apple ID password or authentication token extracted from the user’s computer).
- Elcomsoft Phone Breaker obtains the recovery key and decrypts the encrypted partition.
As a result, you will get an image of the decrypted partition in a raw (.dd) format.
Then you can use the “hdiutil” tool (OS X) or FTK Imager (Windows) to mount the partition and explore the data.
FileVault 2 Passwords
Location: hashed, /var/db/shadow/hash/<GUID>
Extraction (hash): cat /var/db/shadow/hash/<GUID> | cut -c169-216
Recovery (original password): Elcomsoft Distributed Password Recovery
When setting up a FileVault 2 volume, you may be prompted to enable other user accounts to unlock the encrypted volume:
If this is the case, each user must type their password before they will be able to unlock the disk. In order for other users to be able to unlock FileVault 2, one has to click Enable User and enter the user’s password while setting up encryption (or any time after). If new user accounts are added after FileVault 2 encryption is turned on, they are automatically assigned the correct access rights.
Understanding this scheme is very important from the forensic perspective. If there is more than one user on the computer, you’ll have a much greater chance of recovering at least one of these passwords. This is especially true if the computer was used in a household with kids who tend to use much simpler passwords.
In order to unlock an encrypted volume, you will need to use the original plain-text password. Passwords cannot be extracted from a Mac OS X computer; you can only extract password hashes. In order to recover the original plain-text password, you will have to run an attack using a specialized tool such as Elcomsoft Distributed Password Recovery.
With recent update, Elcomsoft Distributed Password Recovery gained the ability to attack plain-text passwords (in addition to user account passwords) protecting disk volumes encrypted with FileVault 2.
Elcomsoft Distributed Password Recovery uses GPU acceleration techniques making the recovery 20 to 50 times faster compared to a CPU alone. You can choose between dictionary attacks with various mutations and GPU-accelerated brute force. Since attacking a password can be lengthy business, Elcomsoft Distributed Password Recovery can utilize multiple computers to simultaneously attack passwords.
Elcomsoft Distributed Password Recovery can recover passwords for popular disk encryption containers. In order to attack a FileVault 2 password with Elcomsoft Distributed Password Recovery, perform the following steps.
Preparing the Attack
- Make an image of the hard drive (physical device) or an image of the encrypted partition and save it into a file. The following formats can be used: Raw disk image (.dd), EnCase image file (.e01), Apple Disk Image (.dmg).
- Run EDPR Disk Encryption Info (EDEI) utility located in Start Menu -> Elcomsoft Password Recovery -> Tools.
- Specify path to the disk image you created on Step 1.
- If more than one encrypted partition is available, specify the volume to attack.
- EDEI will extract the necessary information about the encrypted volume.
- Save the .esprf file created by EDEI.
Running the Attack
- Launch Elcomsoft Distributed Password Recovery.
- Open the .esprf file that was saved by EDEI.
- If several Mac OS accounts appear, choose account to attack.
- Configure the attack (dictionary, mutations, brute force).
- Run the attack.
- Once the password is discovered, you can use it to unlock the Mac that contains the encrypted volume.
Mounting the Volume
After recovering the password to any user account with “Unlock” privileges, you can do the following to mount the encrypted container.
Option 1: [OS X ] In Mac OS X, use “diskutils” to mount the disk volume. Enter the recovered password when prompted. (Applications -> Disk Utility -> File -> Open Disk image -> select image and click Open).
Decrypt Dmg File Without Key Download
Option 2: [OS X ] You can also use Terminal to mount the encrypted image. Launch Terminal and use the following command line to mount the disk image:
hdiutil mount <image>.dd
You can also mount a .dmg image with the following command line:
Decrypt Dmg File Without Key Code
hdiutil mount /<image>.dmg
More information on FileVault 2: https://support.apple.com/en-us/HT204837