8/10 (77 votes) - Download WiFite Linux Free. WiFite for Linux is a great useful tool with which you can audit wireless networks in your area, by automating its functions with a series of instructions. Some of the tools available to audit Wi-Fi networks aren't precisely easy to use. Wifite (easy and automatic) Airodump-ng (easy but not automatic, you manually have to do what wifite did on its own) Wifite Methodology We'll go with the easy one first. Now you need to realize that for a handshake to be captured, there needs to be a handshake. Jun 14, 2017 WEP is an old and depreceated way of protecting WiFi passwords, so if you find one, you are in luck. WEP takes substantially less time. This is easily automated in Wifite, and it even uses multiple attacks against routers to get the password. You only need around 10 to 120 minutes to crack WEP, maybe longer.
- Feb 25, 2016 WiFite Description To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the 'set it and forget it' wireless auditing tool.
- Wifite is a Python-script and it internally uses the Aircrack-ng suite. Apart from this, it has a couple of pre-requisites. But, all of them come pre-installed in Kali Linux.
So you’re interested in Hacking and Cracking? Or just want some free WiFi! Either way you have found the right place to begin.
Today we are going to walk through the steps needed to crack WiFi access points using a combination of wifite and Aircrack-ng. In this guide we will go through how to capture and crack the handshakes to reveal the WiFi Password.
Firstly, you will need a Kali machine! For the purpose of this guide I am using a vanilla install of Kali and am running all of my sessions and commands as a Root user, if you are using a standard account then ‘Sudo’ will be required before most, if not all commands being executed.
The installation of Kali is on a Laptop with a compatible WiFi adapter which allows for monitor mode, this is necessary to capture packets ‘in the air’.
Boot up Kali and either navigate to ‘wifte‘ in the applications tab or open up a terminal and type in ‘wifite‘.
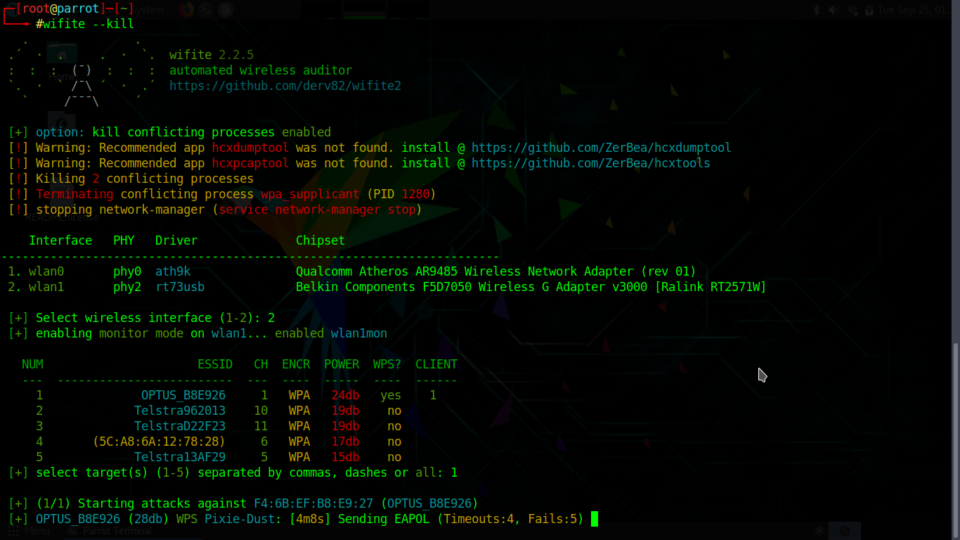
Immediately you will see a list of WiFi SSID’s begin to populate in the terminal window. The key thing to look out for is the amount of connected clients (as we are trying to capture a handshake between the client and the AP).
After choosing the Access Point in wifite in this case ‘EternalWIFI’, it will attempt to deauth the clients connected (disconnect the Clients). Those clients will then try to re-establish a connection and in doing so, wifite will capture the initial handshake packets which contain the password hashes. The more clients that are connected to the AP the better the chance and more quicker wifite will capture the handshake packets.
When a Handshake packet is captured, Wifite will try a default/simple password list. Its not bad and has worked for me a few times on individuals that tether there phones and change their passwords to something very simple, you can of course edit this list to include more passwords.
As you can see from the above, wifite has managed to crack the simple password which is ‘password’.
This however, will not always work and so we will need to crack the hash against a password list. We are going to do this by using aircrack-ng and feeding a password list against the capture handshake hash.
So, we are going to need passwords, a list of passwords to run against the hash.
If you need some password files I have zipped a few up HERE, I have found these on the Internet and take no credit for them!
However, the best way to get wordlists is by creating them yourself on Crunch. If you suspect that someone has changed their password to something ‘personal’ then it might be worth running CUPP (Common User Password Profiler) for a list.
Kali also comes with a default list (rockyou.txt) located in: /usr/share/wordlists
When hashing against a list, the more you know about the network, router and users can help a lot. First things first would be to look at the SSID (most SSID’s have the brand of router included within the name) and this allows you to understand how many characters the default WiFi code is and the combination of letters, numbers, caps. An example of this is:
Default Iphone Hotspots/Tether will use 13 Lowercase only with Numbers (No Symbols or Caps). This information will allow us to filter our wordlists and create new wordlist around this.
Once you have downloaded or created a password list, it’s time to run this against the captured hash using aircrack-ng. The Syntax for aircrack-ng is:
aircrack-ng capturedpackets.cap -w wordlist.txt
When we execute this, aircrack-ng will begin hashing the passwords from the list against the handshake password hash.
If the password is in the list then it will eventually strike a match.
As you can see, the WiFi password is ‘pleaseletmein’. While a simple password, this one wasn’t in the common password file in wifite and required the use of our own wordlist in order to crack.
Make sure you exit monitor mode on your WiFi adapter so you can test if the passphrase works.
So there we have it, the WiFi password. Please note that the cracking speed will be based upon your machines performance and it goes without saying that if the passphrase isn’t in your wordlist then you wont find the password. So make sure you build out specific wordlists dependent on the WiFi AP you want to crack. There are many other tools that you can use for the capture of the handshake and the cracking of the handshake. I prefer wifite as its easy to use and great for beginners and aircrack-ng has easy to remember syntax for piping a handshake to a wordlist.
Please use this knowledge responsibly and make sure you have consent to execute attacks such as this against someones Access Point. I take no responsibility for misuse of this information.
Please feel free to put any questions or comments in the section below.
Written and Executed by Gennaro Migliaccio
Proofed, Edited and otherwise scrutinized by Summer-Jade Greenaway
In this article series, we will look at a tool named Wifite suitable for automated auditing of wireless networks. Most of you who have experience in wireless pentesting would use tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng to crack wireless networks. This would involve a sequence of steps, like capturing a specific numbers of IV’s in case of WEP, capturing the WPA handshake in case of WPA etc, and then subsequently using aircrack-ng to crack the password required for authentication to the network. Wifite aims to ease this process by using a wrapper over all these tools and thus making it super easy to crack Wifi networks.
Here is a list of features of Wifite as per its official homepage.

- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- “anonymous” feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py’s current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
- built-in updater: ./wifite.py -upgrade
Before we start using wifite, make sure you have a proper wireless card that supports packet injection. If you don’t have one, i would suggest that you buy this card.
Note that there is a bug in Wifite that may or may not be there in your particular version of Wifite. The bug basically doesn’t aireplay-ng to function properly and displays an error like aireplay-ng exited unexpectedly . In order to fix this, you will have to make slight modifications in the code of wifite. You can install gedit (apt-get install gedit) which is a text editor and then edit the wifite python script (found in /usr/bin/wifite) using the steps mentioned here. To open wifite, use the command gedit /usr/bin/wifite. This will open up the source code of wifite. Then replace every occurence of cmd = [‘aireplay-ng’, with cmd = [‘aireplay-ng’,‘—ignore-negative-one’,
Wifite can be found under Applications –> Kali Linux –> Wireless Attacks –> 802.11 Wireless Tools. Also, note that if you are running wifite in a different VM than Kali Linux, then you have to make sure that tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng are already installed on that system. This is because Wifite is nothing but a wrapper over all these tools. Before we even start using Wifite, it is better to update to the latest version.
In my case, i already have the latest version. In this tutorial, we will be targeting a simple Wifi network with WEP encryption. Just using the command wifite -h will give you a list of all the commands.
A very tempting option would be -all which tries to attack every network that it finds. We will try it in later articles in this series. However, first lets take a look at all the targets that we have. To do that, use the command wifite -showb
Once this is done, we can see that wifite has put our network interface card into monitor mode (using airmon-ng) and started to look for clients. After a few more seconds, it will start displaying the list of access points.
Note that as it is mentioned in its feature list (automatically de-authenticates clients of hidden networks to reveal SSIDs), this list will also include hidden access points. Hence, wifite can also be used to find hidden access points. In this case we will attack an access point with the BSSID 00:26:75:02:EF:65 that i have set up for testing purposes. The access point has a simple WEP password 1234567890.
To start attacking an access point, just press Ctrl+C. Wifite will now ask you to choose a target number from the list. The target number for my test network is 1, so let me enter that. Note that if you press Ctrl+C again, it will quit Wifite.
Wifite - GitHub
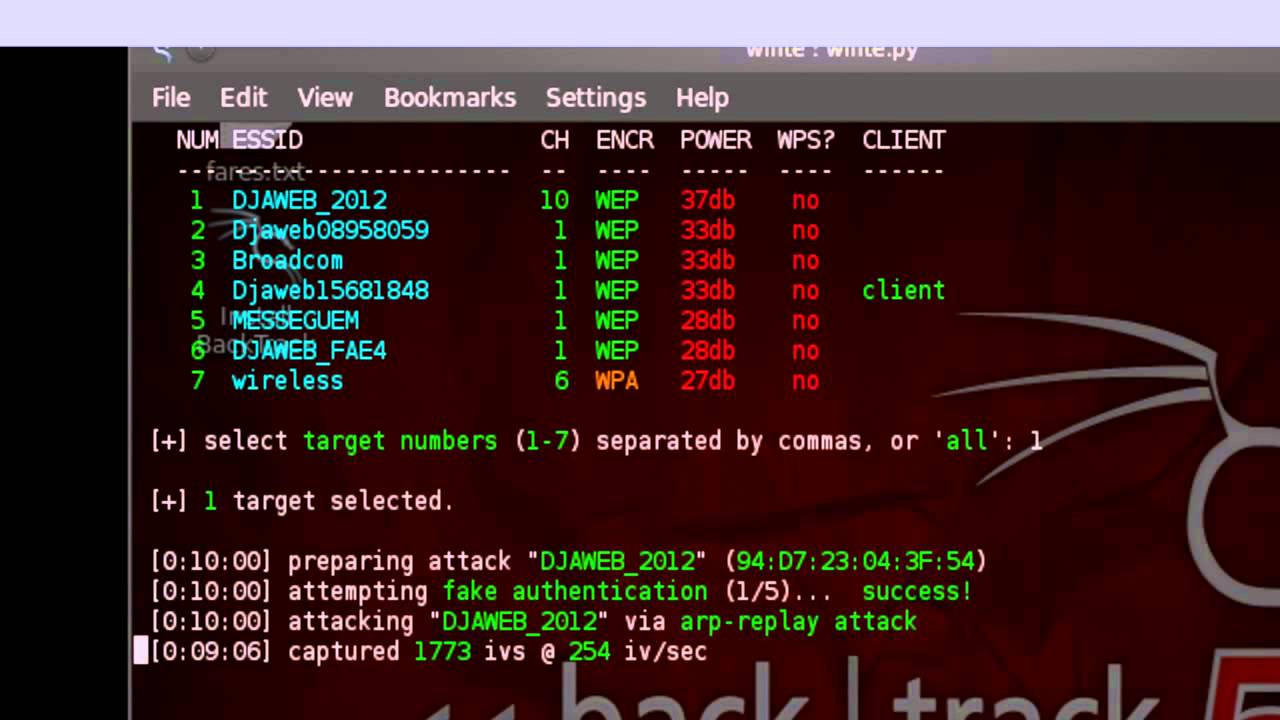
You can now see that Wifite will start attempting to crack the WEP access point using the different known techniques for cracking WEP encryption. After some unsuccessful tries, it has finally begun to start attacking the access points using different techniques for cracking WEP.
Wifite Kali Linux
Once enough IV’s are being captured, it will automatically start cracking the password.
As we can see, Wifite has successfully figured out the WEP key for the access point. Wifite is an extremely useful tool for cracking wireless networks. As i mentioned previously, you need to have all the tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng already installed on your system. To further prove the point, let’s dive into the source code of Wifite.
As we can see, the python code has mentions of calling aireplay-ng. Hence, it is recommended to run Wifite inside Kali linux.
See Full List On Github.com
In the next article, we will look at some advanced usage options of Wifite.